Introduction
Digital forensic investigation has become indispensable in modern crime-solving endeavors, as the proliferation of digital devices has created a vast landscape of potential evidence. In this digital age, forensic technology serves as the key to unlocking crucial digital evidence, shedding light on complex cases, and enabling justice to prevail.
Understanding Digital Forensic Investigation
Digital forensic investigation encompasses the systematic process of uncovering, preserving, analyzing, and presenting digital evidence in legal proceedings. This multifaceted discipline draws upon a combination of technical expertise, legal knowledge, and investigative skills to navigate the digital realm effectively.
The Evolution of Digital Evidence
The advent of technology has transformed the nature of evidence, with traditional physical evidence now complemented by digital counterparts. Digital evidence encompasses a broad spectrum, including emails, social media posts, GPS data, metadata, digital images, videos, and more. This wealth of digital information holds invaluable insights into criminal activities, making it a focal point of forensic scrutiny.
Forensic Technology: Enabling Precision Analysis
At the heart of digital forensic investigation lies forensic technology, a diverse array of tools and methodologies designed to extract, analyze, and interpret digital evidence. From sophisticated software applications to specialized hardware devices, forensic technology empowers investigators to delve deep into digital artifacts, reconstruct timelines, and uncover hidden patterns.
Key Components of Forensic Technology
- Forensic Imaging: By creating bit-by-bit copies of digital storage media, forensic imaging preserves the integrity of evidence while enabling investigators to conduct thorough analyses without altering original data.
- Data Recovery: Leveraging advanced data recovery techniques, forensic experts can retrieve deleted, damaged, or encrypted data, potentially uncovering crucial evidence that adversaries seek to conceal.
- Network Forensics: By scrutinizing network traffic, logs, and communication protocols, network forensic analysis elucidates digital interactions, facilitating the identification of unauthorized access, data breaches, and cyberattacks.
- Mobile Forensics: With the ubiquity of smartphones and tablets, mobile forensics has emerged as a specialized field, encompassing the extraction and analysis of data from mobile devices to reconstruct timelines, uncover communications, and track geographical movements.
- Cloud Forensics: As cloud computing proliferates, forensic experts confront new challenges in preserving and analyzing data stored in remote servers, requiring innovative methodologies to navigate virtual environments and extract relevant evidence.
Challenges and Ethical Considerations
Despite its efficacy, digital forensic investigation faces inherent challenges, including encryption, data obfuscation, privacy concerns, and jurisdictional complexities. Moreover, ethical considerations surrounding the collection, analysis, and presentation of digital evidence underscore the importance of adherence to legal standards and professional ethics.
The Intersection of Digital Forensics and Law Enforcement
Law enforcement agencies rely heavily on digital forensic investigation to combat a myriad of crimes, including cybercrimes, financial fraud, intellectual property theft, terrorism, and more. By harnessing forensic technology, investigators can reconstruct digital footprints, attribute actions to perpetrators, and present compelling evidence in court.
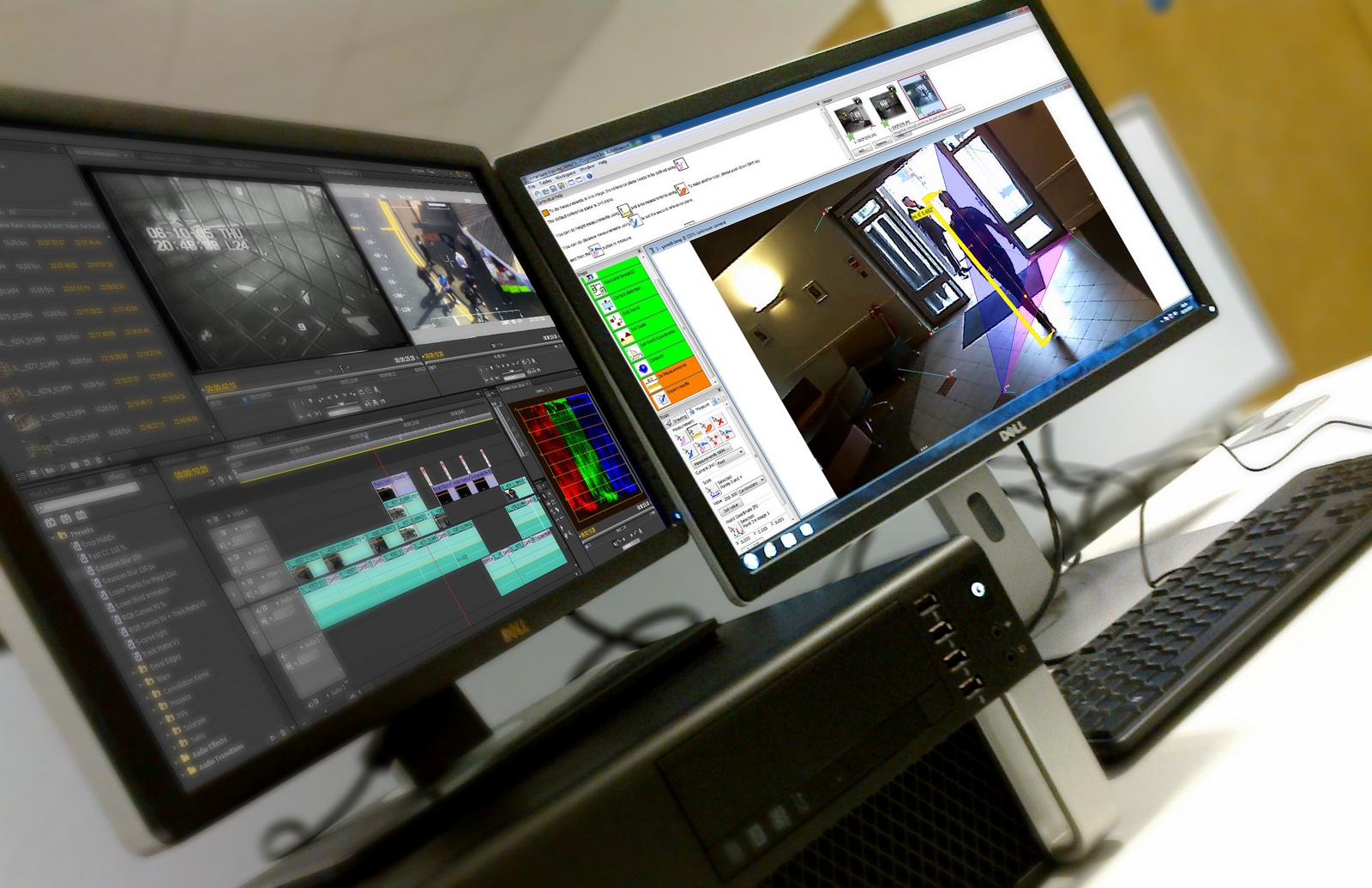
The Role of Digital Forensic Experts
Digital forensic experts play a pivotal role in the investigative process, offering specialized knowledge and technical proficiency to navigate complex digital landscapes. Their expertise extends beyond technical analysis to encompass courtroom testimony, where they elucidate findings, refute challenges, and provide clarity to legal professionals and jurors.
Frequently Asked Questions (FAQs) about Digital Forensic Investigation:
- What is digital forensic investigation?
Digital forensic investigation involves the systematic process of uncovering, preserving, analyzing, and presenting digital evidence in legal proceedings. It utilizes a combination of technical expertise, legal knowledge, and investigative skills to navigate the digital realm effectively. - What types of digital evidence are commonly analyzed in forensic investigations?
Digital evidence encompasses a wide range of digital artifacts, including emails, social media posts, GPS data, metadata, digital images, videos, documents, and more. Each type of evidence can provide valuable insights into criminal activities and is subject to forensic scrutiny. - How does forensic technology aid in digital forensic investigations?
Forensic technology comprises various tools and methodologies designed to extract, analyze, and interpret digital evidence. These tools enable investigators to conduct thorough analyses of digital artifacts, reconstruct timelines, uncover hidden patterns, and present compelling evidence in court. - What are some common challenges faced in digital forensic investigations?
Challenges in digital forensic investigations include encryption, data obfuscation, privacy concerns, jurisdictional complexities, and evolving technologies. Overcoming these challenges requires expertise, innovative methodologies, and adherence to legal standards and professional ethics. - How do digital forensic experts contribute to investigations?
Digital forensic experts play a crucial role in investigations, offering specialized knowledge and technical proficiency to navigate complex digital landscapes. They conduct forensic analyses, testify in court, and provide clarity to legal professionals and jurors, ensuring the integrity and reliability of digital evidence. - What role does digital forensic investigation play in combating cybercrimes?
Digital forensic investigation is essential in combating cybercrimes, including hacking, identity theft, data breaches, malware attacks, and online fraud. By tracing digital footprints, analyzing network traffic, and uncovering digital evidence, investigators can identify perpetrators, attribute actions, and prosecute offenders. - How does mobile forensics differ from other branches of digital forensic investigation?
Mobile forensics focuses specifically on extracting and analyzing data from mobile devices, such as smartphones and tablets. It involves retrieving call logs, text messages, emails, app data, and location information to reconstruct timelines, uncover communications, and track geographical movements. - What ethical considerations are important in digital forensic investigations?
Ethical considerations in digital forensic investigations include respecting privacy rights, obtaining proper authorization for data collection, preserving evidence integrity, and ensuring transparency in methodologies and findings. Adherence to legal standards and professional ethics is paramount to maintaining the integrity and credibility of digital evidence.
These FAQs provide insights into common questions surrounding digital forensic investigation, addressing key concepts, challenges, and ethical considerations in this critical field.
Conclusion:
In the digital age, the significance of digital forensic investigation and forensic technology cannot be overstated. These tools and methodologies serve as the linchpin of modern investigations, unraveling digital evidence that holds the key to justice. As technology evolves, so too must the practices of digital forensic investigation, ensuring its continued relevance and effectiveness in the pursuit of truth and accountability.





